Don’t Lose Everything to Negligence
You might have noticed how productive businesses can be now that the workforce is becoming more and more mobilized. What you might not have noticed,...
 Not Even the World’s Greatest Tech Institutes are Immune to Hacking
Not Even the World’s Greatest Tech Institutes are Immune to Hacking
Recently, a mysterious Indian hacker compromised a sub domain of the Massachusetts Institute of Technology. “Sahoo” restricted his digital mischief to some on-line graffiti posting, “Massachusetts Institute of Technology (MIT) g0t 0wned!!! Shocked??? Indian Hacker –Sadhoo- was here!!!”
No information was stolen during the course of the hack.
MIT was lucky.
Many organizations, companies and educational institutes attract ‘hacktivist’ attention by virtue of their prominence in society. Hackers go after these entities for all sorts of reasons. Some hackers attack organizations on political or philosophical grounds in order to make a “point”. Others are much less noble, simply looking for that digital score of cash or data. Still others are looking to thumb their nose at the establishment and make a name for themselves amongst their peers.
Whatever their motivation, one thing is clear: you don’t want them messing in your playground!
Building an adequate defense against malicious attacks is a key responsibility of IT professionals. Companies who are careless about their security policies and infrastructure may incur significant liability in the event of a data breach.
There are a number of steps a savvy company can take to better safeguard itself. The right combination of hardware, software and information governance policy can help protect you from hackers and other digital ne’er do wells. Properly constructed protections may also help shield your company from liability in the event of a breach.
If you have questions about your Information Security, give us a call at {phone} or send us an email at {email}. {company} can help you protect yourself from hackers and stay up-to-date on the latest security threats.


You might have noticed how productive businesses can be now that the workforce is becoming more and more mobilized. What you might not have noticed,...
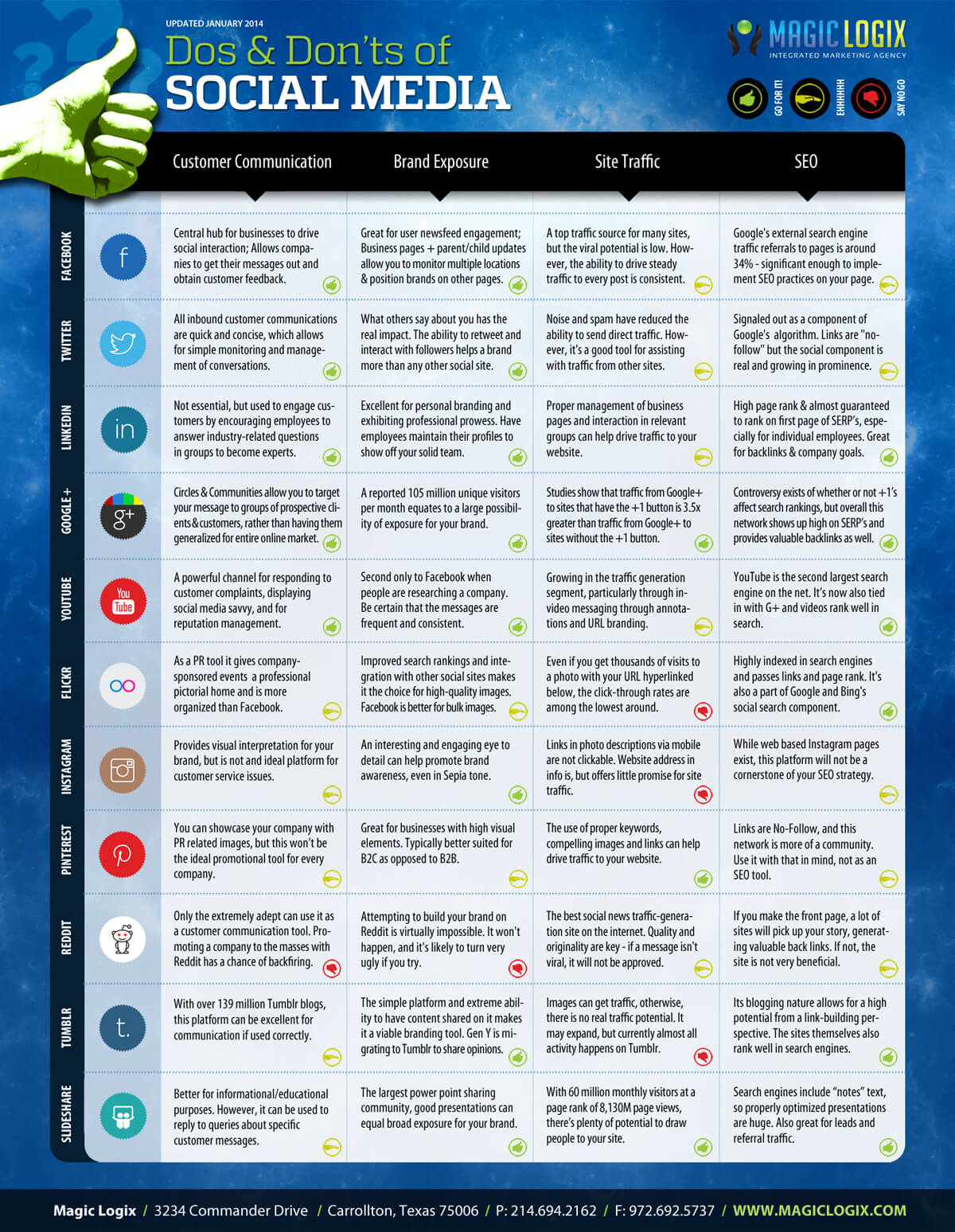
Check out this great infographic from Magiclogix. Click on the graphic below to expand.

Do you know how to customize Windows 10 to fit your needs? If your job requires work on a PC every day, even the smallest details can make a huge...

On Time Tech is an IT Support and Computer Services company serving California. We provide services to the areas in and around We know businesses like yours need technology support in order to run highly-effective organizations. Leverage pro-growth technology services for your company now.
© 2026 On Time Tech