Social Media Do’s & Don’ts For 2014
Check out this great infographic from Magiclogix. Click on the graphic below to expand.
You might have noticed how productive businesses can be now that the workforce is becoming more and more mobilized. What you might not have noticed, however, is just how risky that can be. Encryption can be the difference between saving and losing your business.

A lost and/or stolen laptop can be absolutely devastating if not encrypted. Strong passwords will not prevent a thief from infiltrating your company’s information. They can use your laptop to boot to a new operating system off a USB stick, bypassing the password and looking at your crucial files, such as:
You need to start enhancing security protocols through encryption right away. Why? Because you wouldn’t want all your hard earned work being threatened by some cybercriminal. Full disk encryption will protect your entire device and keep all of your sensitive information out of the wrong hands.
Even if your device is never recovered, you’ll be able to sleep at night knowing it’s impenetrable, regardless of where it is. You may also use file encryption methods to ensure specific documents, files, spreadsheets, and databases are encrypted without encrypting your whole device.
It’s an easy way to mitigate privacy threats of all sorts while using minimal efforts and being able to easily start and use encryption. The infiltrator will only see scrambled and cyphered text, having absolutely no access to your files.
It is also important to always backup your files onsite and offsite and always test by restoring. This way if your device were to ever be lost or stolen, you still have all of your important files with you.
*Note: NEVER forget your encrypted passphrase or you will be locked out of your laptop, and your hard drive will be completely inaccessible.
{company} covers all the bases to secure your business with the highest layers of encryption. You can contact {phone} or email us at {email} to speak to one of our IT specialists.

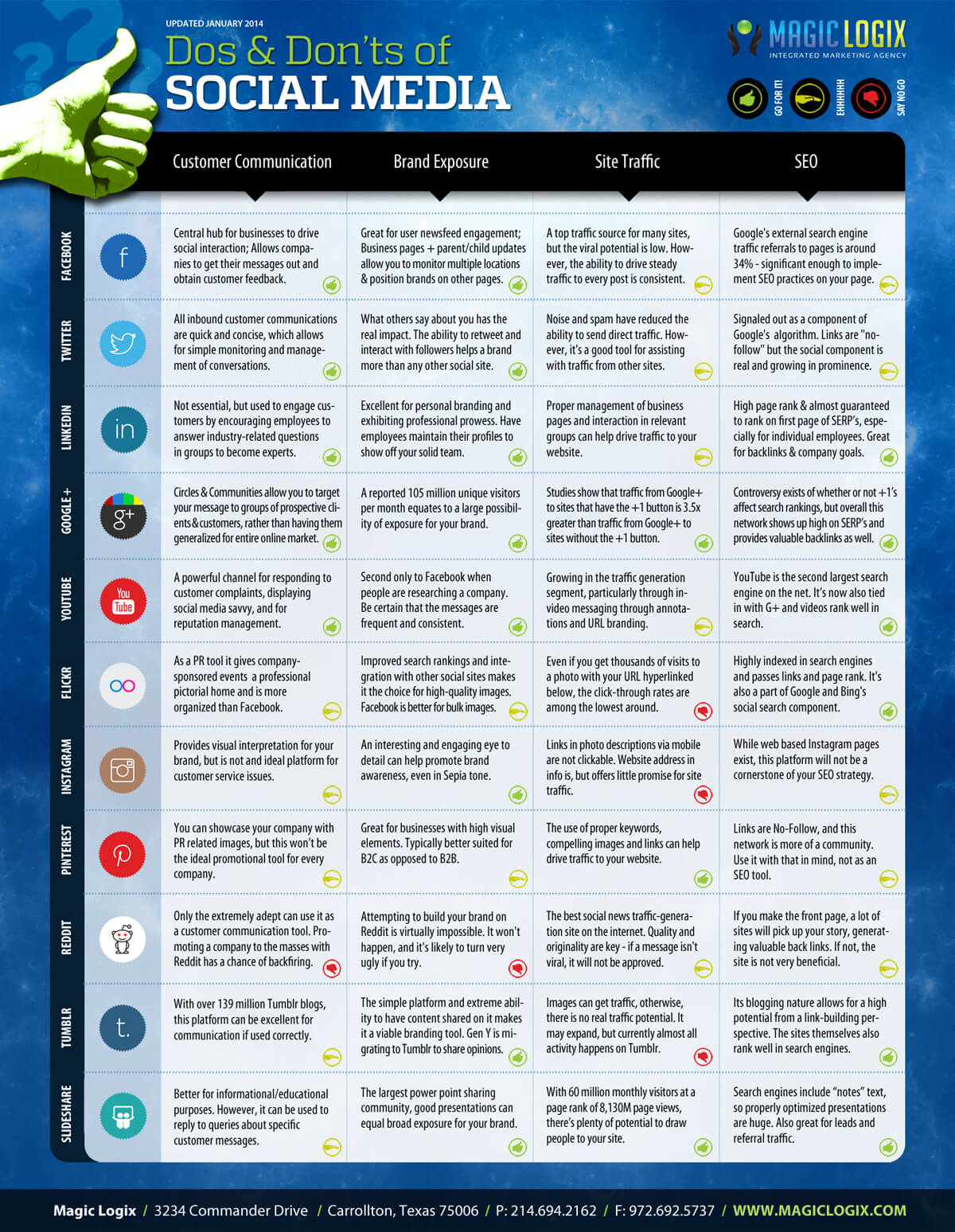
Check out this great infographic from Magiclogix. Click on the graphic below to expand.

Do you know how to customize Windows 10 to fit your needs? If your job requires work on a PC every day, even the smallest details can make a huge...

Don’t Be Surprised When YOUR Network is Hacked – Leaving All of Your Sensitive Data in the Hands of Cybercriminals! Most large companies already...

On Time Tech is an IT Support and Computer Services company serving California. We provide services to the areas in and around We know businesses like yours need technology support in order to run highly-effective organizations. Leverage pro-growth technology services for your company now.
© 2026 On Time Tech